The recent cyberattack on HomeTeamNS, a Singapore-based non-profit that supports national servicemen from the Home Team, has reignited concerns over the rising tide of ransomware threats targeting public sector organisations and critical infrastructure. In this case, swift containment measures—disabling and isolating affected servers—helped limit the damage. Yet, the incident remains a stark reminder that cybercriminals are becoming more targeted, aggressive, and sophisticated.
Such attacks are no longer isolated or opportunistic. According to Semperis, a leader in identity-driven cybersecurity, they reflect a broader global trend. Public sector institutions—traditionally seen as low-risk targets—are now frequently under threat. Often operating with fewer cybersecurity resources than their private-sector counterparts, these organisations are especially vulnerable to threat actors seeking financial gain or classified data.
As ransomware continues to evolve and grow more accessible, Gerry Sillars, Vice President for Asia Pacific and Japan at Semperis, outlines the key vulnerabilities this incident has exposed and offers insights on how organisations can build lasting resilience.
How ransomware attacks are evolving
Over the past five years, ransomware has morphed from basic encryption-based extortion into a sprawling, multi-billion-dollar industry. Today’s threat actors often operate as part of structured, business-like syndicates. A major contributor to this shift is ransomware-as-a-service (RaaS). In this model, developers supply ready-made ransomware kits to affiliates in exchange for a cut of the profits. These kits often come with customer support, dashboards, and step-by-step instructions, drastically lowering the technical barrier to entry.

The result is a sharp rise in ransomware activity across the globe. SonicWall’s 2025 Cyber Threat Report revealed a significant rise in ransomware attacks, with over 6 billion critical network attacks blocked globally in 2024. This marks a continued surge in ransomware incidents, following an 8% increase in North America and an alarming 259% rise in Latin America. The public sector, often seen as vulnerable due to its high-value data and limited cybersecurity resources, remains one of the most frequently targeted sectors.
In the HomeTeamNS case, the absence of a ransom demand suggests the attackers may have been seeking sensitive personal information rather than monetary gain. With the organisation’s links to the Singapore Police Force and Civil Defence Force, the motive may have involved surveillance or data theft—highlighting how political or geopolitical objectives are increasingly behind some ransomware campaigns.

The use of artificial intelligence adds further complexity. Cybercriminals are now employing AI and deepfake technologies to craft convincing phishing emails, impersonate employees in video calls, and automate intrusion attempts. These tools enable more targeted and efficient attacks, often bypassing traditional defences. “We are moving into an era where cybercriminals use artificial intelligence and machine learning to automate and refine their attack strategies. These tools can help attackers bypass traditional security defences, making it essential for businesses to adopt AI-driven security solutions,” notes Sillars. This increasing sophistication calls for a corresponding evolution in defence strategies.
Key lessons from the HomeTeamNS incident
One of the clearest takeaways from the HomeTeamNS response was the effectiveness of swift containment. The organisation’s rapid isolation of compromised servers helped prevent the ransomware from spreading further—demonstrating the value of a well-rehearsed response playbook.
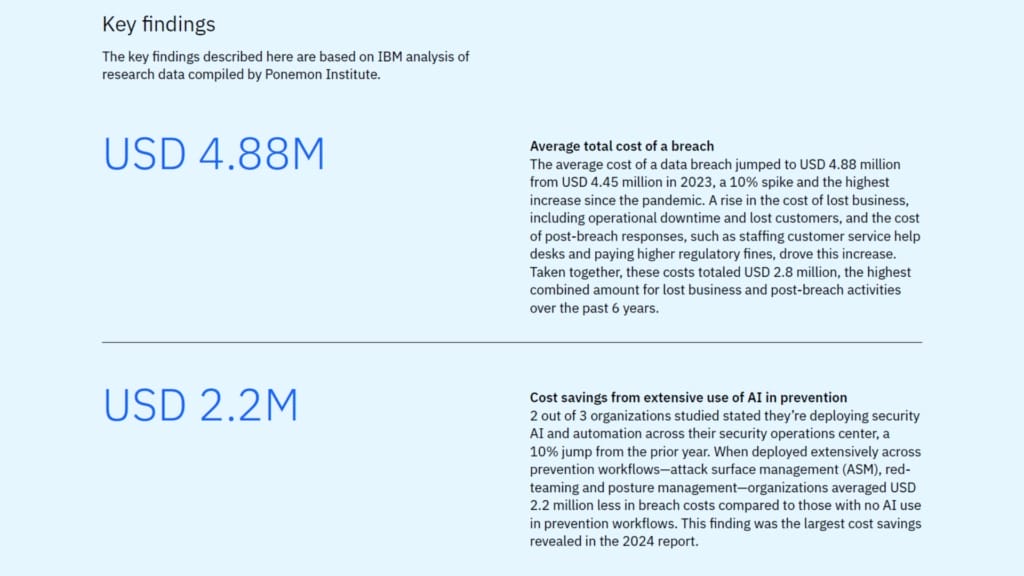
A crucial component of this response was network segmentation. By dividing the network into isolated zones, the organisation limited the malware’s movement and minimised disruption. When combined with Zero Trust security models, this approach significantly reduces an attack’s blast radius. Organisations that adopted layered security approaches—such as network segmentation, Zero Trust architecture, and AI-driven tools—consistently reported lower breach costs. IBM’s 2024 report found that the extensive use of AI and automation alone reduced average breach costs by US$2.2 million.
Yet, segmentation alone isn’t enough. Organisations must adopt a layered defence strategy. This includes deploying advanced endpoint detection and response (EDR) tools to flag suspicious behaviour—such as unexpected file encryption or unusual login activity—before damage is done. A rigorous patch management process is also vital, as many ransomware campaigns exploit known vulnerabilities. For instance, the infamous WannaCry attack in 2017 succeeded largely due to unpatched Windows systems.
Another key defence is staff education. A University of Melbourne study found that nearly 70% of cyberattacks stem from human error, highlighting the importance of regular phishing and social engineering tactics training. While foundational, such awareness initiatives remain one of the most cost-effective forms of risk reduction.
Importantly, compliance alone is not enough. Meeting regulatory requirements is necessary, but it doesn’t guarantee protection. Organisations need to adopt a proactive, threat-informed mindset that anticipates attacks rather than simply responding to them.
Assessing and mitigating ransomware risks
One of the most pressing challenges in the aftermath of a ransomware attack is determining whether data has been stolen. To uncover the scope of a breach, a thorough forensic investigation is essential, analysing logs, traffic flows, and system activity to trace any unauthorised access or data exfiltration.
Quick, coordinated action is key. Having a clear incident response plan—with predefined roles and external cybersecurity partners on standby—can prevent confusion and reduce downtime. “During cyberattacks, the pressure can be overwhelming for organisations, and the instinctual response would be to panic,” says Sillars. “It is critical to set aside any immediate reactions and quickly establish clear roles and responsibilities for the internal response teams.”

The question of ransom payment remains contentious. Semperis strongly discourages paying, noting that it can incentivise further attacks. Data from the company’s 2024 global ransomware study showed that 35% of organisations that paid a ransom received either corrupted files or no data. “Paying ransoms does not guarantee recovery. It fuels the ransomware economy,” Sillars cautions.
Instead, resilience should be the goal. This means maintaining secure, offline backups, enforcing identity and access management controls, limiting privileged access, and monitoring high-risk accounts in real time. These measures can help prevent attackers from gaining a foothold in the first place.
Post-incident reviews are also vital. Every breach offers an opportunity to strengthen defences. By identifying what went wrong, updating incident playbooks, and conducting tabletop simulations, organisations can better prepare for future threats.
Future cybersecurity strategies and trends
As ransomware threats grow more intelligent and unpredictable, organisations must evolve their strategies accordingly. Attackers already use AI to identify weak spots, automate reconnaissance, and scale campaigns. To counter this, defenders must also harness AI—using machine learning tools to detect anomalies, automate response workflows, and gain real-time visibility into account activity.
An auspicious approach is a zero-trust architecture. By operating on the principle that no user or device should be trusted by default, Zero Trust limits access to only what’s necessary. This minimises the risk of lateral movement within a compromised network. Gartner estimates that by 2026, at least 60% of organisations will have adopted some form of Zero Trust—up from under 20% in 2022.
Stronger regulations and collaborative efforts will also play a critical role. In Singapore, initiatives like the Cybersecurity Act and Critical Information Infrastructure (CII) framework are driving higher security standards. Public-private partnerships will be essential for sharing intelligence and building coordinated responses to large-scale threats.
For businesses looking to strengthen their cyber resilience in 2025, the guidance is clear: identify critical assets, assume a breach is inevitable, test recovery plans regularly, and invest in technologies that provide actionable insights. As the threat landscape evolves, the focus shifts from simply stopping an attack to ensuring the organisation can withstand and recover from it.





